Hardwired TCP/IP Chapter 7: W55MH32 DNS Example for Domain Name Resolution
Hardwired TCP/IP Chapter 7: W55MH32 DNS Example for Domain Name Resolution
Hardwired TCP/IP Chapter 7: W55MH32 DNS Example for Domain Name Resolution
In this article, we will provide a detailed explanation on how to implement the DNS domain name resolution function on the W55MH32 chip. Through practical examples, we will guide you on how to convert the wiznet.io domain name into the actual IP address, for your reference.
Other network protocols used in this routine, such as DHCP, please refer to the relevant sections. Regarding the initialization process of the W55MH32, please also refer to the relevant sections. We will not elaborate on it here.
1 Introduction to the DNS Protocol
Before learning the DNS protocol, let's first clarify the concepts of IP address and domain name:
- IP Address: A long string of numbers that uniquely identifies a computer on the network.
- Domain Name: Also known as a domain, it is a name composed of a series of names separated by dots on the Internet, serving as the identifier for a single computer or a group of computers during data transmission, for locating purposes. For example: wiznet.io.
How to understand the concepts of domain names and URLs? One way to think about it is that URLs contain domain names. For instance: https://wiznet.io/Products is a URL, and wiznet.io is the domain name.
Because IP addresses have the disadvantages of being difficult to remember and not being able to display the names and characteristics of the address organization, domain names were designed, and the domain name resolution protocol (DNS, Domain Name System) was used to map domain names and IP addresses to each other, allowing people to access the Internet more conveniently without having to remember the long string of IP addresses that can be directly read by machines. Mapping a domain name to an IP address is called DNS forward resolution, and mapping an IP address to a domain name is called DNS reverse resolution.
The DNS protocol can be transmitted using UDP or TCP, and the port number used is 53, but in most cases, DNS is transmitted using UDP.
The above is a brief introduction to the DNS protocol. If you want to have a deeper understanding of this protocol, please refer to the introduction on the Mozilla website: DNS - MDN Web Glossary: Definitions of Web-related Terms | MDN
2 Introduction to DNS Domain Names
DNS domain names are generally classified into the following categories:
- Root Domain Server: The root domain server is at the top level of the DNS system and is responsible for managing the root zone (Root Zone) of the entire DNS namespace. It is mainly used to guide queries and point to the authoritative servers of top-level domains (TLDs).
- Top-Level Domain Server: It is responsible for resolving specific top-level domains (such as .com, .org, .net) or country/region code top-level domains (ccTLDs, such as .cn, .uk).
- Authoritative DNS Server: It is responsible for storing and providing DNS record information for a specific domain.
- Local DNS Server: The local domain server is the default domain server used by the computer for resolution, that is, the preferred DNS server and alternative DNS server set in the computer. Common ones include local DNS services provided by telecom, unicom, Google, Alibaba, etc.
3 DNS query method
DNS query methods are divided into the following two types:
- Recursive Query: Refers to the query request initiated by the DNS client (such as the user device or local domain name server) to the DNS server. The DNS server is responsible for completing the entire query process and returning the final resolution result to the client.
- Iterative Query: Refers to the next suggestion returned by the DNS server to the client or the requester, rather than directly returning the final result. The client needs to perform multiple queries on its own to gradually obtain the resolution result.
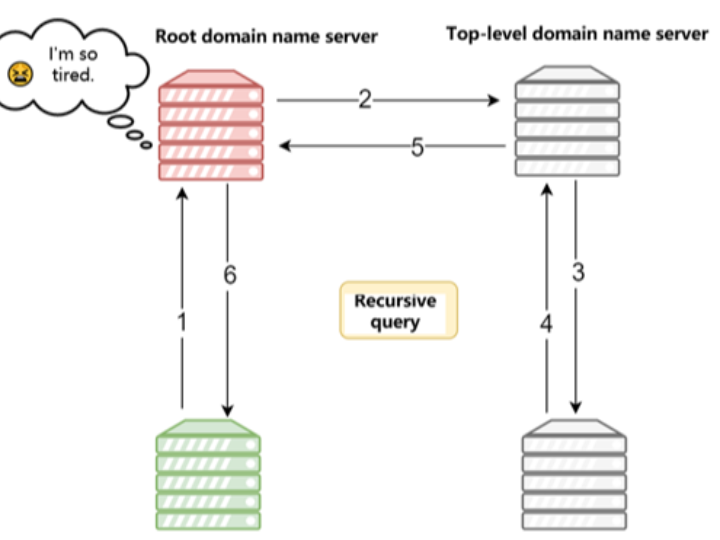
The two diagrams below are the workflow diagrams of recursive query and iterative query.
4 The basic workflow of the DNS protocol
Next, let's take the example of PC correctly resolvingwww.baidu.com to understand the workflow of DNS resolution.
1) First, search for "DNS cache of the browser", where a table mapping domain names to IP addresses is maintained;
2) If no match is found, continue to search for "DNS cache of the operating system";
3) If still no match is found, the operating system will send the domain name to the "local domain name server", and the local domain name server will query its own DNS cache to look for a match. If successful, the result will be returned (note: the query method between the host and the local domain name server is "recursive query");
4) If the DNS cache of the local domain name server does not have a match, the local domain name server will query the upper-level domain name server through the following "iterative query" method (note: the query method between the local domain name server and other domain name servers is iterative query to prevent excessive pressure on the root domain name server):
- First, the local domain name server makes a request to the "root domain name server". The root domain name server is at the highest level and it does not directly indicate the IP address corresponding to this domain name. Instead, it returns the address of the top-level domain name server, meaning it points the local domain name server in the right direction to search for the answer.
- After obtaining the address of the "top-level domain name server", the local domain name server then makes a request to it to obtain the address of the "authorization domain name server". Local domain name server
Make a request to the address of the permission domain name server, and finally obtain the corresponding IP address for that domain name.
5) The local domain name server will return the obtained IP address to the operating system, and at the same time cache the IP address itself.
6) The operating system will return the IP address to the browser, and at the same time cache the IP address itself.
7) At this point, the browser has obtained the IP address corresponding to the domain name and has cached it.
For a more intuitive understanding, please refer to the following diagram:
Network client
When using DNS forward resolution for the wiznet.io domain name on the W55MH32, we only need to send a DNS request message to the local domain server, and then parse the DNS response message.
5 DNS message
DNS messages are divided into the following five parts:
- Message header: Defines the meta-information of the request or response (such as flags, number of entries, etc.).
- Question area: Describes the domain name and query type of the query.
- Answer area: Contains the final result of the query (such as the IP address corresponding to the domain name).
- Authoritative area: Provides information of the authoritative DNS server.
- Additional area: Contains additional relevant information (such as the A record of the domain name).
The DNS request message mainly consists of the message header and the question area. The answer area, authoritative area and additional area are all empty.
1.Message header
- Transaction ID: Fixed length of 16 bits, a unique identifier used for matching requests and responses.
- Flags: Fixed length of 16 bits, flags (such as query type, recursion expectation, etc.).
- Questions: Fixed length of 16 bits, the number of entries in the question area, usually 1.
- Answer RRs: Fixed length of 16 bits, the number of entries in the answer area, 0 in the query message.
- Authority RRs: Fixed length of 16 bits, the number of entries in the authoritative area, 0 in the query message.
- Additional RRs: Fixed length of 16 bits, the number of entries in the additional area, 0 in the query message.
2. Problem Area
- QName: The domain name being queried (stored in dot-separated form).
- QType: The type of record being queried (such as A record, AAAA record, MX record, etc.).
- QClass: The category of the record being queried, usually IN (Internet).
The DNS response message contains a similar header and question area to the request message, and also includes answer, authoritative and additional area information.
1. Message header: Similar to the request message, but the Flags content has changed:
QR: indicates a response (0 in the query message).
RCODE: Return code, indicating the response status (e.g., 0 means no error, 3 means the domain does not exist).
AA: Authority answer flag (1 indicates this is the response returned by the authoritative server).
2. Question area: Consistent with the request message, used to describe the client's query.
3. Answer area: Contains the query results, such as the IP address corresponding to the domain name. Each answer includes the following fields:
- Name: The corresponding domain name
- Type: Record type (such as A, AAAA, CNAME, etc.).
- Class: Record category (usually IN).
- TTL: Record's lifetime (seconds).
- Rdata: The specific value of the record (such as an IP address).
4. Authoritative area: Provides information about the authoritative server, usually including NS records.
5. Additional area: Contains additional resolution information, such as the A record and AAAA record of the authoritative server.
Request message example: Request to resolve the A record for the domain name wiznet.io
| Message Header | Transaction ID: 0x8D12Response message example: The DNS server returned the A record resolution result for wiznet.io (with the IP address 183.111.138.249)
| Message Header | Transaction ID: 0x8D126 The implementation process
Next, let's take a look at how to implement DNS forward resolution on the W55MH32.
Note: Since this example requires access to the internet, please ensure that the configuration of the W55MH32 enables internet access.
Step 1: Register the DNS timer interrupt to the 1-second timer.
1. /**The registration of DNS timer interrupt is mainly for handling DNS timeouts.
In the dns.h file, the DNS timeout time, retry count, port number and message ID, etc. are defined:
1. #ifndef _DNS_H_Step 2: Perform DNS forward resolution processing
In the do_dns() function, we have implemented the process of DNS forward resolution.
1. do_dns(ethernet_buf, dns_name, ip_fromdns);The three parameters of this function are the DNS resolution cache required, the domain name to be resolved, and the IP address after resolution.
The content of the do_dns() function is as follows:
1. /**First, the DNS_init() function will be called to initialize the DNS configuration:
1. /* DNS CLIENT INIT */Then, in the DNS main loop, the DNS execution function DNS_run is executed. Its main function is to perform DNS packet packaging, send requests, parse response content, and handle timeouts. Here, only corresponding processing needs to be carried out based on the return value of the DNS_run() function.
The content of the DNS_run() function is as follows:
1. /* DNS CLIENT RUN */7 Run results
After the burning routine was executed, the PHY link was first detected, then the DHCP process was used to obtain the network address result, and finally DNS successfully resolved the IP address of wiznet.io to 183.111.138.249, as shown in the following figure:
8 Summary
This article describes the method of implementing DNS domain name resolution on the W55MH32 chip, explaining how to resolve the wiznet.io domain name to the actual IP address. It elaborates on the concepts of DNS protocol, domain classification, query methods and workflow, and introduces the structure of DNS messages as well as example request and response messages. It also demonstrates the implementation process on the W55MH32. The next article will explain the implementation of HTTP Client function on this chip, introducing the principle and implementation steps of submitting data to a specified website. Please stay tuned!
WIZnet is a non-fabrication semiconductor company founded in 1998. Its products include the Internet processor iMCU™, which adopts TOE (TCP/IP Offloading Engine) technology and is based on a unique patented fully hardwired TCP/IP. iMCU™ is designed for embedded Internet devices in various applications.
WIZnet has over 70 distributors worldwide, with offices in Hong Kong, South Korea, and the United States, providing technical support and product marketing.
The region managed by the Hong Kong office includes: Australia, India, Turkey, and Asia (excluding South Korea and Japan).
