Hardwired TCP/IP Chapter 26: Example of Host Computer Search and Configuration for W55MH32
Hardwired TCP/IP Chapter 26: Example of Host Computer Search and Configuration for W55MH32
Hardwired TCP/IP Chapter 26: Example of Host Computer Search and Configuration for W55MH32
In this article, we will provide a detailed explanation on how to implement the upper machine search and configuration functions on the W55MH32 chip. Through practical examples, we will guide you on how to search for W55MH32 devices in the local area network via the upper machine and configure their network addresses. The example code includes an open-source upper machine configuration tool named SmartConfigTool, which supports searching for devices, setting network address parameters, and firmware upgrade functions.
For other network protocols used in this example, such as DHCP, please refer to the relevant sections. Regarding the initialization process of W55MH32, please refer to the "Network Install" chapter. We will not elaborate on this here.
1 Introduction to the Host Computer
Embedded Host refers to the upper-level device in an embedded system that communicates, controls, and exchanges data with the embedded equipment. It usually has stronger computing capabilities and storage resources, and is used to control and monitor the operation of lower-level embedded devices (such as sensors, actuators, embedded controllers, etc.).
2 Characteristics
- Efficiency: Configuring the upper computer to control the lower computer can significantly enhance the efficiency of the control system. The upper computer issues control commands, and the lower computer receives and interprets them as corresponding timing signals to directly control the equipment. The response speed is fast and the reliability is high.
- Real-time performance: The lower computer can respond to the control instructions from the upper computer in real time and perform real-time control of the equipment, ensuring the stability and security of the system. At the same time, the lower computer can also provide real-time feedback of equipment status data to the upper computer, enabling the upper computer to promptly understand the system status and make corresponding control adjustments.
- Flexibility: The upper computer and the lower computer can be flexibly combined and expanded to meet the requirements of different systems. The upper computer can simultaneously connect multiple lower computers to monitor, control, and process data for them. At the same time, the lower computer can also connect multiple devices as needed to achieve distributed control of the equipment.
- User-friendly interaction: The upper computer usually has a human-computer interaction interface, providing users with a friendly graphical interface or text interface, facilitating operation, configuration, and monitoring.
3 Application scenario
The W55MH32 can be used with the NetBIOS protocol for the following applications:
- Industrial Automation: The upper computer issues control instructions, and the lower computer receives and interprets them as corresponding timing signals to directly control the equipment. The response speed is fast and the reliability is high. The upper computer can monitor the production process, issue control instructions, conduct data analysis and optimization, etc. The lower computer can control the equipment in real time, collect equipment status data, receive and execute control instructions, etc.
- Internet of Things: The upper computer can remotely monitor and manage the equipment, conduct data analysis and processing, etc. The lower computer can receive and execute control instructions, collect and transmit equipment status data, etc.
- Smart Home: The upper computer can issue control instructions, monitor the home network, etc. The lower computer can receive and execute control instructions, control the operation and status collection of intelligent devices, etc.
- Medical Equipment: The upper computer can issue control instructions, remotely monitor and manage medical equipment, etc. The lower computer can receive and execute control instructions, control the operation and status collection of medical equipment, etc.
4 The basic workflow of searching and configuring
Search: The host computer sends the "FIND" command via UDP broadcast. The device, acting as the slave computer, will then send its own configuration information to the host computer upon receiving it. After receiving the information, the host computer will display the obtained device details.
Configuration: Based on the devices that have been searched for, the host computer sends the "SETT" command to the device. Upon receiving the command, the device will reconfigure itself according to the network information displayed by the host computer and display it on the serial port.
5 The implementation process
Next, we implement the upper computer search and reply function as well as the upper computer configuration function on W55MH32.
Note: The test instance requires that the PC and W55MH32 be on the same network segment.
First, within the main loop, the do_udp_config() function is called. The do_udp_config() function is continuously run.
1. while (1)The do_udp_config() function continuously handles operations related to UDP configuration, including receiving commands from the host computer, performing different operations based on the commands, such as receiving network information query requests and returning network information, or receiving network configuration information and updating local network information, etc.
The do_udp_config() function is as follows:
1. void do_udp_config(uint8_t sn)First, a UDP state machine will be run. When a message is received, the instruction will be evaluated. If it is the "FIND" instruction, the network address information of the device will be read and sent back. If it is the "SETT" instruction, the address issued by the upper computer will be updated in the W55MH32.
6 Run results
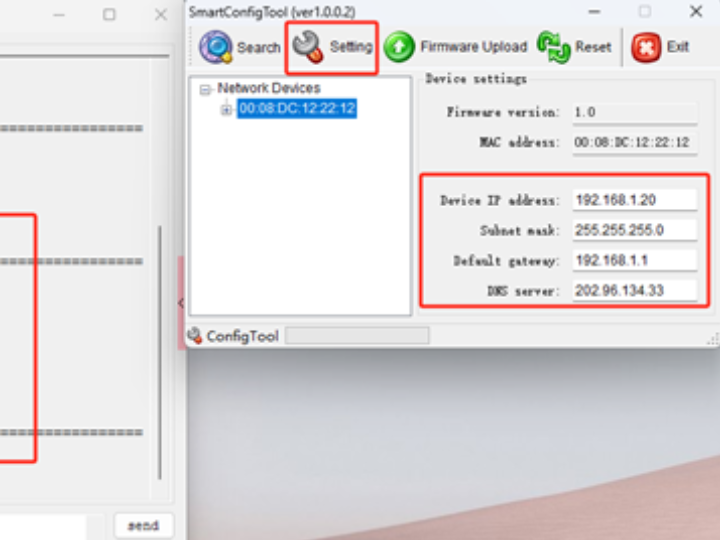
After the burning routine is executed, the PHY link detection is carried out first, then the network address is obtained through DHCP and the network address information is printed. The information printed on the serial port is observed to obtain the device operation status. After waiting for the device to print the relevant network information, the ConfigTool upper computer tool is opened, and clicking Search allows you to see that the upper computer has successfully obtained and presented the device information. Then the IP address is modified, and clicking Setting allows you to see that the serial port has printed the network information after the upper computer's configuration, as shown in the following figure:
Upper computer search for equipment:
The upper computer modifies the network configuration information:
7 Summary
This article explains how to implement the upper computer search and configuration functions on the W55MH32 chip. Through practical examples, it demonstrates the process of using the open-source upper computer configuration tool SmartConfigTool to search for W55MH32 devices in the local area network and configure their network addresses. The article details the concept, characteristics, application scenarios, and basic workflow of the upper computer, helping readers understand its practical application value in embedded device management.
The next article will focus on using the TOE interrupt function on the W55MH32 chip, analyzing the core principle and application of the TOE interrupt function, and explaining through practical examples how to use interrupts for loopback data testing. Stay tuned!
WIZnet is a non-fabrication semiconductor company founded in 1998. Its products include the Internet processor iMCU™, which adopts TOE (TCP/IP Offloading Engine) technology and is based on a unique patented fully hardwired TCP/IP. iMCU™ is designed for embedded Internet devices in various applications.
WIZnet has over 70 distributors worldwide, with offices in Hong Kong, South Korea, and the United States, providing technical support and product marketing.
The region managed by the Hong Kong office includes: Australia, India, Turkey, and Asia (excluding South Korea and Japan).
