Hardwired TCP/IP Chapter 18: W55MH32 FTP Server Example
Hardwired TCP/IP Chapter 18: W55MH32 FTP Server Example
Hardwired TCP/IP Chapter 18: W55MH32 FTP_Server Example
In this article, we will provide a detailed explanation on how to implement the FTP protocol on the W55MH32 chip. Through practical examples, we will also explain various functions such as using the W55MH32 as an FTP server, the PC as an FTP client for file transfer, directory operations, etc.
Other network protocols used in this example, such as DHCP, please refer to the relevant sections. Regarding the initialization process of the W55MH32, please refer to the "Network Installation" chapter. We will not elaborate on this here.
1 Introduction to the FTP Protocol
FTP (File Transfer Protocol) is a standard network protocol used for transferring files between clients and servers. The FTP client protocol is implemented based on the FTP protocol and is used to guide the client on how to communicate with the FTP server, enabling functions such as file upload, download, and directory operations. Since FTP was originally designed for plaintext transmission and is not secure enough, adding an SSL/TLS encryption layer to FTP can provide encrypted control connections and data connections. The following is an introduction to the main content and working mechanism of the FTP client protocol.
2 Characteristics of the FTP Protocol
- Based on TCP transmission: FTP uses two TCP connections: the control connection (port 21) and the data connection (port 20 or the dynamically assigned port in PASV mode), ensuring reliable data transmission.
- Separate control from data:
- The control connection is used for sending commands and receiving responses.
- The data connection is used for transmitting file contents or directory information.
3 Support multiple transmission modes:
- Active Mode: The server initiatively connects to the data port of the client.
- Passive Mode: The client initiatively connects to the data port provided by the server, addressing the limitations imposed by NAT firewalls.
4 Support multiple file operations:
- File upload (STOR), download (RETR), deletion (DELE).
- Directory operations (MKD, RMD, CWD, PWD).
- Obtaining file list (LIST, NLST).
5 Clear-text transmission (traditional FTP): Usernames, passwords and data are transmitted in plain text, which is insecure. Security improvements: FTPS (FTP Secure, based on SSL/TLS) and SFTP (Secure File Transfer Protocol, based on SSH).
6 Flexible user authentication mechanism:
- Support anonymous login (anonymous users can use email as the password).
- Support authentication of username and password.
3 Application scenarios of the FTP protocol
Next, let's take a look at what operations and applications can be accomplished using the FTP protocol on the W55MH32?
Firmware upgrade: Embedded devices can upgrade their systems by downloading new firmware or software update packages via FTP. This is suitable for devices that require regular updates, such as routers and industrial control equipment.
Data collection and transmission: Embedded devices (such as sensor nodes or data recorders) upload the collected data to remote servers for storage and analysis. For example, environmental monitoring equipment uploads temperature and humidity data to the server.
Remote configuration and log management: Devices can download configuration files or upload log information for administrators to analyze and troubleshoot. This is suitable for industrial automation equipment and embedded monitoring systems.
Embedded Web server file management: Many embedded devices have a simple Web server built-in for file storage or content distribution. These files can be managed through FTP.
4 The basic workflow of the FTP protocol
1. Establish a control connection
- Client initialization: The client starts the FTP client program and specifies the address and port number (port number is 21) of the FTP server to connect to.
- TCP connection establishment: The client initiates a connection request to the 21 port of the server via the TCP protocol. The server listens to this port, receives the request, and establishes a TCP connection with the client. This connection is called the control connection and is mainly used for transmitting FTP commands and server response information.
- Authentication: After the connection is established, the server prompts the client to enter the username and password for authentication. The client sends the corresponding username and password information to the server. After the server verifies the information, it allows the client to proceed with subsequent operations. There are also anonymous FTP servers that allow users to use "anonymous" as the username and an email address as the password for login, providing public file access services.
2. Selection of Transmission Mode
The client and the server negotiate the data transmission mode during the control connection. There are mainly two modes:
- Active mode (PORT mode): The client informs the server through the control connection of its own data port (a randomly opened port by the client), and the server initiatively connects to the client's data port using port 20 to transmit data.
- Passive mode (PASV mode): The client sends the PASV command to the server, and the server informs the client of a temporary data port it has opened (usually a port above 1024), then the client uses a random port of its own to connect to the server's this temporary data port to transmit data.
3. Data transmission
According to the user's operational requirements, perform file or directory-related operations through data connection:
- Upload file: The client sends the STOR (storage) command to the server, and then transmits the local file data through the data connection to the server. After receiving the data, the server stores it in the specified directory.
- Download file: The client sends the RETR (retrieve) command to the server, requesting to download the file on the server. The server sends the file data through the data connection to the client, and the client receives the data and saves it to the local designated location.
- Directory operations: The client can also send commands such as LIST (list directory contents), CWD (change working directory), MKD (create directory), RMD (delete directory), etc. The server executes the corresponding operations and returns the operation results through the control connection. When executing these commands, if it is necessary to transfer directory lists and other data, it will also be transmitted through the data connection.
4. Close the connection
- Data connection closed: After completing file transfer or other operations, the data connection will be closed. If there are other operations that need to be performed, the client and the server can re-establish the data connection as needed.
- Control connection closed: When the client completes all operations, it will send the QUIT command to the server. After receiving the command, the server will close the control connection. At this point, the FTP session between the client and the server ends.
5 Explanation of Active Mode and Passive Mode
Active Mode:
- The client opens a port and starts listening.
- The client informs the server of its own IP and port through the control connection.
- The server actively connects to the port specified by the client and transmits data.
Passive Mode:
- The client initiates the connection request in a passive mode.
- The server opens a random port and informs the client through the control connection.
- The client then initiatively connects to the port specified by the server and transmits data.
Comparison of advantages and disadvantages:
- The active mode is more suitable for environments where there are no firewall restrictions on the server-side network.
- The passive mode is more appropriate for situations where the client is behind a NAT or firewall.
6 FTP Message Analysis
FTP messages are divided into command and response messages. Command messages are used to send operation requests, while response messages are used to return results.
The format of command messages is "<command> <parameters>\r\n", and the field explanations are as follows:
<Command>: FTP commands (such as USER, PASS).
<Parameter>: Additional information for the command (such as username, file name).
For example, "USER username\r\n". Common commands include login (USER, PASS), file operations (RETR, STOR), directory operations (LIST, CWD), etc. Each FTP message consists of the command or response code, status code, and additional data. The status code is used to indicate the operation result.
Here are the common FTP commands:
- USER: Provide the username for identity verification.
- PASS: Provide the password for identity verification.
- CWD: Change the current working directory.
- PWD: Display the current working directory.
- LIST: List the files and subdirectories in the directory.
- RETR: Download files from the server.
- STOR: Upload files to the server.
- DELE: Delete the specified file.
- MKD: Create a new directory.
- RMD: Delete the directory.
- QUIT: Terminate the session and exit.
- TYPE: Set the file transfer type (ASCII or Binary).
- PORT: Specify the port for the data connection.
- PASV: Enable passive mode, where the server specifies the port for the client to connect to.
The response message format is "<status code> <description>\r\n", and the field explanations are as follows:
- <Status Code>: The three-digit number represents the status.
- <Description Text>: The textual description of the status.
For example, "230 User logged in, proceed.\r\n". Here are some common response codes for FTP:
- 1xx (Informative Response): This mainly provides some initial information and usually indicates that the server is processing the request but has not completed the operation yet.
- 2xx (Successful Response): This indicates that the command has been successfully executed. This is one of the response types that clients most desire, as it means that the operation of the request (such as login, file transfer, etc.) has been completed successfully.
- 3xx (Informational Response): This indicates that the server requires some additional information to complete the operation. This usually occurs during processes such as authentication or file location.
- 4xx (Temporary Error Response): This indicates that there is a problem with the client's request, but the error is temporary and can be resolved by some adjustments (such as re-sending the request, etc.).
- 5xx (Permanent Error Response): This indicates that there is an error with the client's request, and this error is relatively serious and difficult to correct through simple adjustments.
Next, let's take a look at an example of the FTP message for obtaining a directory:
- The client establishes a TCP connection to the server's port 21.
- The server responds: 220 Welcome to FTP Server\r\n
- The client sends: USER wiznet\r\n
- The server responds: 331 User wiznet OK. Password required\r\n
- The client sends: PASS wiznet\r\n
- The server responds: 230 User logged in\r\n
- The client sends: PORT 192,168,1,5,20,100\r\n (Active mode. 192,168,1,5 is the client's address, 20,100 is the client's expected port number, 20*256+100 = 5260)
- The server responds: 200 PORT command successful\r\n
- The client sends: LIST\r\n (DIR command, to obtain the file information of the current directory)
- The server replies: 150 Opening ASCII mode data connection for file list\r\n
- The server initiates a TCP connection to the client's expected port number and transmits the directory information. After the transmission is completed, it closes the TCP connection.
- The client sends: QUIT\r\n (To exit the FTP session)
- The server responds: 221 Goodbye\r\n
7 The implementation process
Next, let's take a look at how to implement the Server mode of the FTP protocol on the W55MH32. Note: The test instances require that the PC and W55MH32 be on the same network segment.
Step 1: Obtain network configuration information and initiate FTP.
1. wizchip_getnetinfo(&net_info);The content of the ftpd_init() function is as follows:
1. void ftpd_init(uint8_t *src_ip)The main function of the ftpd_init() function is to initialize various parameters of the FTP server, including server status, user authentication information, network address and port, as well as creating a TCP socket to prepare for the subsequent operation of the FTP service.
Step 2: Achieve continuous interaction between the server and the client
The ftpd_run() function is continuously called in the main loop, and its function is to make the FTP server run continuously, constantly processing various requests from the client, achieving continuous interaction between the server and the client, and providing stable FTP services.
1. while (1)
2. {
3. ftpd_run(ethernet_buf);
4. }
The content of the ftpd_run() function is as follows:
1. uint8_t ftpd_run(uint8_t *dbuf)After entering the ftpd_run() function, the program will execute a state machine in TCP Server mode (refer to the TCP Server section for details). When the socket is in the SOCK_ESTABLISHED state, if it is the first time entering this state, a welcome message will be sent to the client. Subsequently, it will listen for client instructions. When a client instruction is received, it will enter the proc_ftpd() function for processing.
The proc_ftpd() function handles FTP service commands and performs corresponding operations based on different commands and parameters, including user authentication, file operations, data transmission, status handling, and error responses.
Note: When the value of the macro definition connect_timeout_en is set to 1, the connection timeout function will be enabled. If no operation is performed after the duration defined by the macro definition remain_time has elapsed, the system will automatically disconnect the connection. Here, connect_timeout_en is a macro that controls the enabling or disabling of the connection timeout function, with a value of 1 indicating that the function is enabled and 0 indicating that it is disabled; while remain_time is a macro that defines the maximum allowable period of no operation before triggering the automatic disconnection operation.
The proc_ftpd() function is as follows:
1. char proc_ftpd(uint8_t sn, char *buf)After entering the proc_ftpd() function, the program will execute a state machine. Firstly, it converts the received command to lowercase and searches it in the command table. If not found, it sends an error message. Before login, only the USER, PASS, and QUIT commands are allowed, and any other commands will result in an error. For different commands, such as USER_CMD, it handles username verification and subsequent operations, PASS_CMD performs password verification and login, TYPE_CMD handles transmission type settings, FEAT_CMD sends feature information, QUIT_CMD disconnects the connection, and RETR_CMD and other file operation commands, as well as PORT_CMD and PASV_CMD, which are related to data connection modes, perform corresponding operations and error handling based on different situations, and send the corresponding status information.
8 Run results
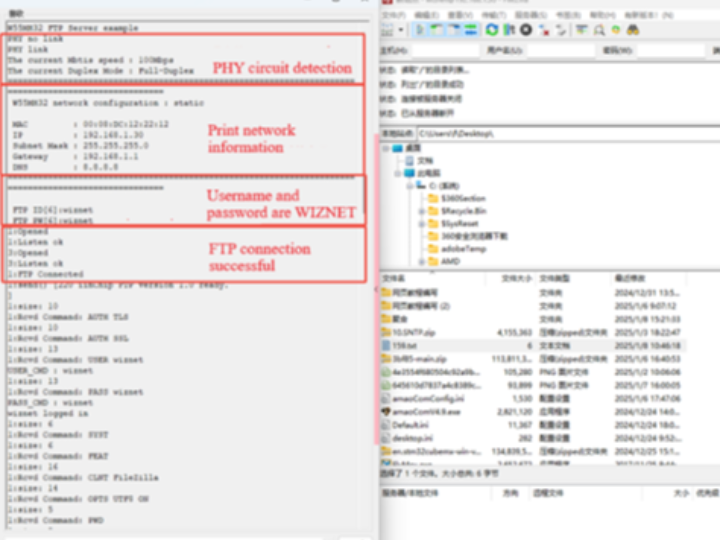
After the burning routine is executed, the PHY link detection is first carried out, followed by the printing of the network information settings. Open the FileZilla software (download link: Client - FileZilla Chinese Website), and fill in the host ID, username, password, and port number (usually 21) on the FileZilla software to connect to the FTP server. If the connection is successful, the following interface will be displayed:
Then, drag the local site files to the remote site (server), and the files were successfully transferred to the server.
9 Summary
This article explains how to implement the FTP server mode on the W55MH32 chip. Through practical examples, it demonstrates the process of using W55MH32 as an FTP server and performing file transfer, directory operations, and other functions with the PC end. It covers key steps such as obtaining network configuration information and FTP initialization, as well as achieving continuous interaction between the server and the client. The article details the concept, characteristics, application scenarios, basic workflow, active and passive modes, and message parsing of the FTP protocol, helping readers understand its practical application value in file transfer.
The next article will focus on the FTP client mode, analyzing its core principles and applications in file transfer, and explaining how to implement the FTP client function on W55MH32. Stay tuned!
WIZnet is a non-chipfoundry semiconductor company founded in 1998. Its products include the Internet processor iMCU™, which adopts TOE (TCP/IP Offloading Engine) technology and is based on a unique patented fully hardwired TCP/IP. iMCU™ is designed for embedded Internet devices in various applications.
WIZnet has over 70 distributors worldwide, with offices in Hong Kong, South Korea, and the United States, providing technical support and product marketing.
The region managed by the Hong Kong office includes: Australia, India, Turkey, and Asia (excluding South Korea and Japan).
