Hardwired TCP/IP Chapter 17: W55MH32 ARP Example
Hardwired TCP/IP Chapter 17: W55MH32 ARP Example
Hardwired TCP/IP Chapter 17: W55MH32 ARP Example
In this article, we will provide a detailed explanation on how to implement the MAC RAW mode on the W55MH32 chip. Through practical examples, we will also explain to you how to use the MAC RAW mode to perform ARP to convert IP addresses into MAC addresses.
Other network protocols used in this example, such as DHCP, please refer to the relevant sections. Regarding the initialization process of the W55MH32, please refer to the Network Install section. We will not elaborate on this here.
1 Introduction to the MACRAW Model
The MACRAW mode is a low-level communication mode provided by W55MH32 TOE. The chip directly receives and sends Ethernet frames without parsing the protocols of the TCP/IP layer. Through this mode, users can directly manipulate the headers of Ethernet frames (such as destination MAC address, source MAC address, Ethernet type, etc.) and the payload data.
Note: Only Socket0 can be set to the MACRAW mode.
2 Introduction to the ARP Protocol
ARP (Address Resolution Protocol) is a network protocol used to resolve the corresponding MAC address based on the known IP address. It operates at the second layer (data link layer) of the OSI model and is an important component of local area network communication in IPv4 networks.
3 Characteristics of the ARP Protocol
Protocol scope: The ARP protocol operates only within the same local area network (LAN) because broadcast requests cannot pass through routers.
Cache mechanism: To reduce frequent broadcasts, devices will cache the corresponding relationship between IP and MAC for a certain period of time.
Protocol types: ARP request (Opcode = 1): Used to query the MAC address of the target device.
ARP response (Opcode = 2): Used to reply to the ARP message from the requesting party.
4 The workflow of the ARP protocol request
When the sending host A needs to communicate with the target host B, but only knows the IP address of the target host and does not know the MAC address of the target host, and there is no corresponding relationship in its own ARP cache table, the ARP request process will be triggered:
1. Construct ARP request: The sending host needs to construct an ARP request data packet.
2. Broadcast ARP request: The sending host encapsulates the constructed ARP request into an Ethernet frame and sends it to the local area network using the broadcast method.
3. Target host receives and processes: All hosts in the network will receive the broadcast frame, but only the target host (with the matching IP address) will respond.
4. Sending host receives the ARP response and updates its own ARP cache table.
5 Application scenarios of the ARP protocol
- Address Resolution: When a device needs to conduct link layer communication, it can use the ARP protocol to obtain the MAC address of the other device.
- Network debugging and diagnosis: When debugging an embedded device, sending an ARP request can be used to verify the network connectivity of the device.
6 Security Risks of the ARP Protocol and Protective Measures
Although the ARP protocol is extremely important in local area network communication, it also has security risks. For instance, ARP spoofing is a common attack method. Attackers can deceive other devices by forging ARP responses, thereby stealing sensitive information or interrupting network communication. To prevent ARP spoofing attacks, the following measures can be taken:
1. Using Static ARP Table: By configuring static ARP entries, it is possible to limit and specify that devices communicating with the IP address only use the designated MAC address. Thus, even if attackers send forged ARP messages, they cannot modify the mapping relationship between the IP address and MAC address in this table.
2. Port Security and Static IP/MAC Binding: Enable the Port Security function on the access switch and statically bind the user's IP/MAC address. This method can prevent users from sending fake ARP information for the gateway.
3. Dynamic ARP Inspection (DAI) and DHCP Monitoring: Use the combination of Dynamic ARP Inspection and DHCP Monitoring functions to perform legality detection on the ARP messages sent by users and filter out those that do not comply with the rules.
4. Encrypted Communication Protocol: By using encrypted communication protocols, network traffic can be prevented from being eavesdropped and tampered with.
5. Firewall and Switch Configuration: Set corresponding security policies on the firewall and switch, such as enabling special ARP message filtering functions.
6. Client Management: Ensure that all terminal devices follow the security policies and update and patch them regularly.
7 The working principle of the ARP protocol
Send ARP request:
When device A needs to communicate with device B, it first checks if the MAC address of device B is present in the ARP cache. If the MAC address of device B is not found in the ARP cache, device A will send a broadcast ARP request message in the following format: "Who is the IP address X.X.X.X? Please tell me (device A's IP address and MAC address)."
Receive ARP response:
After receiving the broadcast request, device B checks whether the IP address in the request matches its own. If it does, device B sends a unicast ARP response message to device A, informing device B of its MAC address. After receiving the response, device A caches the MAC address of device B for subsequent communication.
8 ARP message format
A standard ARP message consists of the following fields, with a total length of 28 bytes (excluding the link layer frame header):
Field Name | Length (bytes) | Description |
Hardware Type | 2 | Indicates the hardware type. The common value is 1 (Ethernet). |
Protocol Type | 2 | Indicates the protocol type to be resolved. The common value is 0x0800 (IPv4). |
Hardware Address Length | 1 | The length of the hardware address (MAC address), usually 6 bytes. |
Protocol Address Length | 1 | The length of the protocol address (IP address), usually 4 bytes (IPv4). |
Operation Code | 2 | Indicates the operation type: 1 (request), 2 (response). |
Sender Hardware Address | 6 | The MAC address of the requester. |
Sender Protocol Address | 4 | The IP address of the requester. |
Target Hardware Address | 6 | The MAC address of the target device. This field is 0 in the request. |
Target Protocol Address | 4 | The IP address of the target device. |
Detailed Explanation of Message Fields
1. Hardware Type (Hardware Type): Describes the type of network being used, for example:
- 1: Ethernet.
- 6: IEEE 802 network.
For Ethernet ARP packets, this value is always 0x0001.
2. Protocol Type (Protocol Type): Indicates the type of protocol to be parsed, for example:
- 0x0800: Indicates IPv4 address resolution.
- 0x86DD: Indicates IPv6 (usually replaced by the ND protocol instead of ARP).
3. Hardware Address Length (Hardware Address Length): Defines the length of the hardware address (MAC address), usually 6 bytes (Ethernet).
4. Protocol Address Length (Protocol Address Length): Defines the length of the protocol address (IP address), usually 4 bytes (IPv4).
5. Operation Code (Operation Code): Describes the operation type of ARP:
- 1: ARP request.
- 2: ARP response.
6. Sender Hardware Address (Sender Hardware Address): Contains the MAC address of the requesting device.
7. Sender Protocol Address (Sender Protocol Address): Contains the IP address of the requesting device.
8. Target Hardware Address (Target Hardware Address): In ARP requests, this field is empty (all 0s). In ARP responses, it contains the MAC address of the target device.
9. Target Protocol Address (Target Protocol Address): Contains the IP address of the target device.
Message content:
ARP Probe Request Packet:
|Message Analysis|
|Original Message| 00 01 08 00 06 04 00 01 00 08 dc 12 22 12 00 00 00 00 00 00 00 00 00 00 c0 a8 01 69
ARP Request Message:
|Message Analysis||Original Message| 00 01 08 00 06 04 00 01 00 08 dc 12 22 12 c0 a8 01 69 00 00 00 00 00 00 c0 a8 01 8a
ARP response message:
|Message Analysis|
|Original Message| 00 01 08 00 06 04 00 02 64 4e d7 b1 37 11 c0 a8 01 8a 00 08 dc 12 22 12 c0 a8 01 699 The implementation process
Next, let's take a look at how to implement an ARP request on the W55MH32.
Note: The test instance requires that the PC and the W55MH32 be in the same network segment.
Step 1: Call the do_arp() function within the main loop to execute the ARP request process.
1. while (1)The do_arp() function is as follows:
1. void do_arp(uint8_t sn, uint8_t *buf, uint8_t *dest_ip)After entering this function, the program will execute a state machine. When the socket status is in the closed state, a MACRAW mode socket will be opened. Once the socket is successfully opened in the MAC RAW mode, the arp_request() function will be executed to send an ARP request, and then a loop will be entered. When a response is successfully received, the arp_reply() function will be executed to parse the request. If no response is received within 5 seconds, the ARP request fails. When the arp_succ_flag flag is set to 1, it indicates that the ARP request was successful.
The arp_request() function is as follows:
1. void arp_request(uint8_t sn, uint16_t port, uint8_t *dest_ip)In this function, the ARP packets are assembled and sent.
The arp_reply() function is as follows:
1. void arp_reply(uint8_t sn, uint8_t *buff, uint16_t rlen)In this function, we will verify the received ARP message. If the ARP message is a response message and the IP address in the response matches the IP address we requested, we will set the arp_succ_flag flag to 1, indicating that the ARP request was successful.
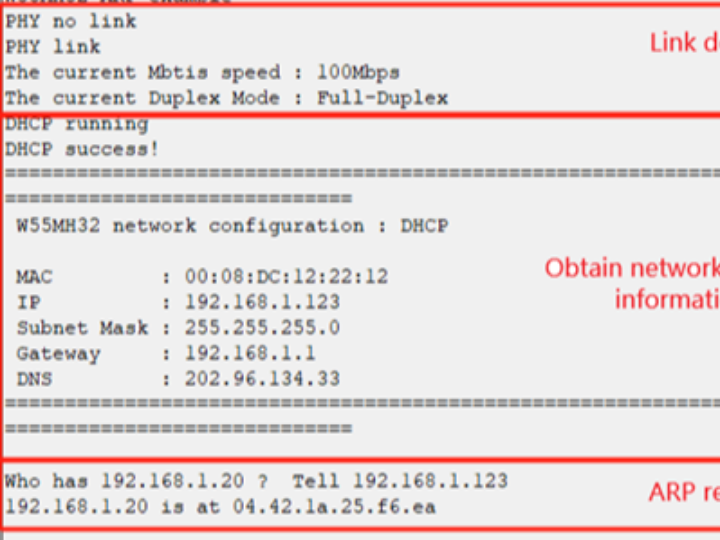
10. Running results
After the burning routine is executed, the following can be observed: Firstly, a PHY link detection is carried out. Then, the set network address information is printed. Next, an ARP request is executed and the result is shown, as depicted in the following figure:
11 Summary
The article explains how to implement the ARP protocol on the W55MH32 chip using the MAC RAW mode, converting IP addresses into MAC addresses. It demonstrates the complete process from sending an ARP request to receiving and processing the response through practical examples. The article provides a detailed introduction to the concepts, characteristics, workflow, application scenarios, security risks and protection measures, as well as the message format of the MAC RAW mode and the ARP protocol. It helps readers understand its practical application value in local area network communication.
The next article will focus on the FTP protocol server mode, analyzing its core principles and applications in file transfer, and explaining how to set up an FTP server on related devices. Stay tuned!
WIZnet is a non-chipfoundry semiconductor company founded in 1998. Its products include the Internet processor iMCU™, which adopts TOE (TCP/IP Offloading Engine) technology and is based on a unique patented fully hardwired TCP/IP. iMCU™ is designed for embedded Internet devices in various applications.
WIZnet has over 70 distributors worldwide, with offices in Hong Kong, South Korea, and the United States, providing technical support and product marketing.
The region managed by the Hong Kong office includes: Australia, India, Turkey, and Asia (excluding South Korea and Japan).
