Hardwired TCP/IP Chapter 16: W55MH32 PING Example
Hardwired TCP/IP Chapter 16: W55MH32 PING Example
Hardwired TCP/IP Chapter 16: W55MH32 PING Example
In this article, we will provide a detailed explanation on how to implement the IPRAW function on the W55MH32 chip. Through practical examples, we will also explain to you how to use the IPRAW mode to implement the PING command in the ICMP protocol for network connectivity testing.
Other network protocols used in this example, such as DHCP, please refer to the relevant sections. Regarding the initialization process of the W55MH32, please refer to the Network Install section. We will not elaborate on this here.
1 Introduction to the IPRAW Model
2 PING Introduction
PING is a command used to test network connectivity and diagnose network issues. It accomplishes this by sending "echo request" messages using ICMP (Internet Control Message Protocol) and waiting for "echo reply" messages, thereby checking whether the target host is reachable and the response time of the network. The PING command is one of the most common tools in network diagnostic tools, and is typically used to verify network connectivity, detect network latency, and troubleshoot network faults, etc.
3 Characteristics of the PING command
1. Simplicity: The PING design is very simple, usually based on the request-response model. One device sends a PING request packet, and the other device responds with a PING response packet. Its overhead is small, making it suitable for the network communication needs of embedded devices.
2. Low latency: Due to the simplicity of PING, the network latency is very low, making it suitable for scenarios that require real-time detection of device status or maintaining heartbeats.
3. Status monitoring and heartbeat: PING is often used for heartbeat detection between devices.
4. No payload data: The data transmitted by PING usually has no payload or additional data; it only contains simple request and response fields, so the network load is very small.
5. Fault tolerance and retry mechanism: Some implementations may have timeout and retry mechanisms to ensure the reliability of PING responses.
4 PING application scenarios
Next, let's take a look at what operations and applications can be accomplished using PING on the W55MH32?
- Network connectivity test: This can be used to test whether the network between the local device and the target device is connected.
- Network troubleshooting: When there is a problem with the network, such as being unable to access a certain website or unable to communicate with a specific device, the PING command can be used to gradually locate the problem. If the PING request to the target device times out or has severe packet loss, it indicates possible network connection interruption, router configuration errors, firewall blocking, etc.
- Network device status monitoring: In network management, it is necessary to monitor the status of various devices (such as servers, routers, switches, etc.) in the network in real time. The PING command can be used to test these devices regularly, and based on whether a response is received to determine if the device is operating normally.
5 The basic workflow of the PING command
1.Send a request
When the user enters the PING command and the IP address or domain name of the target host in the command line, the system begins to construct the ICMP echo request data packet. This data packet contains the ICMP protocol header and a certain amount of data, typically 32 bytes. Subsequently, this data packet is handed over to the IP layer.
The IP layer adds control information such as the source IP address and the destination IP address to the data packet, assembling it into a complete IP data packet. Then, the MAC address of the target host needs to be obtained. If the target host is in the same network segment as the source host, the IP layer will query the local ARP cache table. If there is a corresponding mapping, the MAC address will be directly obtained; if not, an ARP request broadcast will be sent to obtain it. If the target host and the source host are not in the same network segment, the IP layer will hand over the data packet to the routing for processing. The router will forward it based on the routing table, and the router also needs to obtain the MAC address of the next hop.
After the data link layer obtains the target MAC address, it constructs a data frame, encapsulates the IP data packet within it, attaches the source and destination MAC addresses and control information, and then sends the data frame out.
2. Receiving response
After the target host receives the data frame, it checks the destination MAC address. If they match, it receives and extracts the IP data packet and hands it over to the IP layer. The IP layer verifies it is correct and then passes it to the ICMP protocol.
The ICMP protocol constructs an ICMP echo response data packet, copies the data from the request packet, and then hands it over to the IP layer. The IP layer encapsulates it into an IP data packet, and the data link layer builds a new data frame with the source host as the destination address and sends it out.
3. Result Processing
After the source host receives the response data packet, the data link layer and the IP layer process it in sequence. The ICMP response packet is handed over to the ICMP protocol. The ICMP protocol records the current time and calculates the round-trip time by combining the timestamp when the request was made. If multiple request packets are sent, the system will count the number of data packets that did not receive a response and calculate the packet loss rate. Through the round-trip time and the packet loss rate, users can determine the connectivity and quality of the network.
6 Message parsing
ICMP (Internet Control Message Protocol, the protocol used for transmitting control messages between network devices, is typically employed for network diagnosis and error reporting. ICMP messages consist of a type field, a code field, a checksum, and a data section. Common types of ICMP messages include echo request (ping) and echo reply, unreachable destination, timeout, etc.
Here is the basic format of ICMP echo request and response messages:
Field name | Length (bytes) | Echo request value | Echo response value | Description |
Type (Category) | 1 | 8 | 0 | Identify the type of ICMP message |
(Code) | 1 | 0 | 0 | Together with the type field, determine the specific type of the ICMP message. |
Checksum | 2 | It was calculated that | It was calculated that | Used to verify the integrity of the entire ICMP data packet |
Identifier | 2 | Send process ID | The same as the request | Used to identify the messages sent by the sending end |
Serial Number (Sequence Number) | 2 | Increasing serial numbers | The same as the request | The sequence number used to identify the order of the messages sent by the sending end |
Data | Variable | User-defined | The same as the request | Including the data to be returned to the sender, |
|Message Analysis|
|Original message|7 The implementation process
Next, we implement the PING command on the W55MH32. Note: The test instances require that the PC and W55MH32 be on the same network segment.
The do_ping() function plays a role in controlling the PING operation process. It determines whether to continue the PING operation and whether to close the Socket connection after the operation is completed.
This function needs to be called in the main loop, as shown in the following figure:
1. while (1)The do_ping() function is as follows:
1. void do_ping(uint8_t sn, uint8_t *remote_ip, uint8_t req_num)The do_ping() function requires three parameters to be passed in, namely the socket number, the target host IP, and the number of PING requests.
If req is greater than req_num, it indicates that the specified number of PING requests has been reached. At this point, the close() function is called to close the specified Socket connection, and then the function returns, ending this PING operation.
If req is less than req_num, the ping_count() function is called. The PING operation is mainly carried out within the ping_count() function. After entering this function, the following steps will be executed.
The ping_count() function is as follows:
1. void ping_count(uint8_t s, uint16_t pCount, uint8_t *addr)After entering this function, the program will execute a state machine. First, it initializes cnt to 0 and starts a for loop. Different operations are performed based on the state of the Socket. When the Socket is in the state of SOCK_CLOSED, the Socket is closed, the protocol is set, a Socket in the Sn_MR_IPRAW mode is created, and the Socket state is waited to change to SOCK_IPRAW. When the Socket is in the state of SOCK_IPRAW, a ping request is sent, and the inner while loop is entered. If the received length is greater than 0, the ping reply is processed. If no reply is received for a certain period of time, the timeout information is output. At the same time, counting and delay processing will be performed based on cnt. By default, no processing is done. When the conditions are met, the ping request, reply, and statistics of lost requests are output.
Step 1: Send PING request
The ping_request() function is called in the ping_count() function when the Socket state is SOCK_IPRAW, thereby achieving the sending of PING requests according to the set number of times.
The ping_request() function is as follows:
1. void ping_request(uint8_t s, uint8_t *addr)The main function of the ping_request is to send a Ping request. Firstly, some request parameters are initialized, including the request type, code, randomly generated ID and sequence number, data is filled in and the checksum is calculated. Then, the sendto() function is used to send the request, and corresponding information is output based on the sending result, including failure prompts and the address information of the request target.
Step 2: Receive and parse the PING reply:
In the ping_count() function, the ping_reply() function is called when it detects that there is data in the Socket receive buffer (rlen > 0), thereby achieving the parsing and processing of the received PING reply. The ping_reply() function is responsible for receiving and parsing the PING reply data packet, performing corresponding processing based on different data packet types, and printing relevant information after successful parsing.
The ping_reply() function is as follows:
1. void ping_reply(uint8_t s, uint8_t *addr, uint16_t rlen)The ping_reply() function is mainly used to handle the received information. It receives data through recvfrom, determines whether it is a reply or a request based on the header information of the data packet, extracts and parses the relevant information, calculates the checksum and performs the check, outputs information according to different situations (such as error messages, reply source information, or request source information), and sets the receiving status flag.
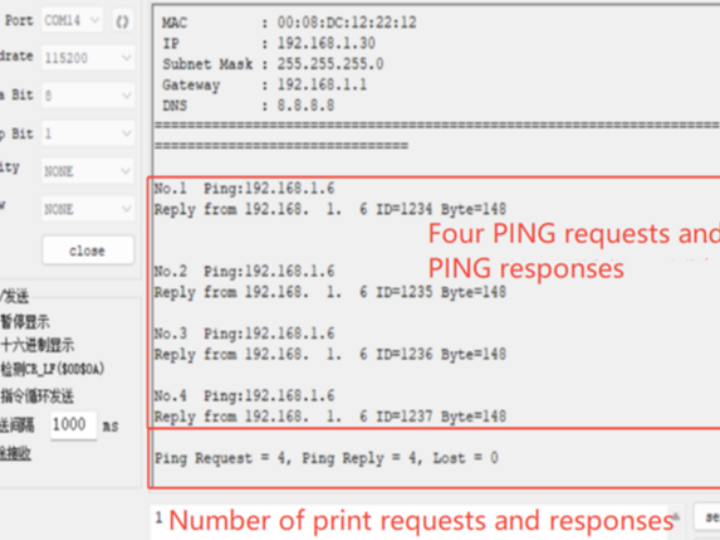
8 Run results
After the burning routine was executed, the PHY link was first detected, then the network information was printed, and finally the ping to the target IP received a response, as shown in the following figure:
9 Summary
This article explains how to implement the PING command in the ICMP protocol using the IPRAW mode on the W55MH32 chip, for network connectivity testing. Through practical examples, it demonstrates the complete process from sending the PING request, receiving and parsing the reply, to statistical results. The article details the concepts, characteristics, application scenarios, basic workflow, and message parsing of the IPRAW mode and the PING command, helping readers understand their practical application value in network testing and fault diagnosis.
The next article will focus on the ARP protocol, explaining its core principles and applications in network communication, and also explaining how to implement the ARP protocol on the W55MH32 chip. Stay tuned!
WIZnet is a non-chipfoundry semiconductor company founded in 1998. Its products include the Internet processor iMCU™, which adopts TOE (TCP/IP Offloading Engine) technology and is based on a unique patented fully hardwired TCP/IP. iMCU™ is designed for embedded Internet devices in various applications.
WIZnet has over 70 distributors worldwide, with offices in Hong Kong, South Korea, and the United States, providing technical support and product marketing.
The region managed by the Hong Kong office includes: Australia, India, Turkey, Asia (excluding South Korea and Japan).
