Hardwired TCP/IP Chapter 14: W55MH32 TFTP Example
Hardwired TCP/IP Chapter 14: W55MH32 TFTP Example
Hardwired TCP/IP Chapter 14: W55MH32 TFTP Example
In this article, we will provide a detailed explanation on how to implement the TFTP protocol on the W55MH32 chip. Through practical examples, we will also explain to you how to use the TFTP client mode to obtain text files from the server.
Other network protocols used in this example, such as DHCP, please refer to the relevant sections. Regarding the initialization process of the W55MH32, please refer to the Network Install section. We will not elaborate on this here.
1 Introduction to the TFTP Protocol
The TFTP (Trivial File Transfer Protocol) protocol is a lightweight file transfer protocol, which is commonly used in scenarios requiring fast and simple file exchange, especially during the startup and configuration of network devices. Unlike FTP (File Transfer Protocol), TFTP is designed very simply, only providing basic file reading and writing functions, and uses UDP as the transport layer protocol, thus lacking the complexity and retransmission mechanism of TCP.
2 Characteristics of the TFTP Protocol
Simplicity: The TFTP protocol is designed simply. Its header format is concise, and the types of operation commands are few, which makes it relatively easy to implement and requires less resource consumption.
Lightweight: The TFTP protocol does not require complex connection establishment and management processes. It has low overhead and is therefore suitable for use in environments with low performance requirements and limited resources.
Based on UDP: TFTP uses UDP as the transport layer protocol, taking advantage of UDP's fast transmission and connectionless characteristics, enabling fast data transmission. However, this also means that TFTP does not provide reliable transmission guarantees and requires reliability mechanisms to be implemented at the application layer.
Port fixed: TFTP uses the fixed port 69 to listen for client requests. The port used for data transmission is dynamically allocated, and a temporary port is selected for each transmission.
Data block size limit: Each data packet can transmit a maximum of 512 bytes of data. If the file is large, it will be transmitted in multiple parts, with each sending a 512-byte data block. The last data block may be less than 512 bytes, indicating the end of the file.
3 Application scenarios of the TFTP protocol
Next, let's take a look at what operations and applications can be accomplished using the TFTP protocol on the W55MH32?
Firmware upgrade: For network devices such as routers and switches, the TFTP protocol is often used to transfer firmware to these devices for firmware updates. The TFTP protocol ensures that firmware files are transmitted to the target devices quickly and accurately.
Configuration file transfer: The TFTP protocol is also commonly used to manage the configuration files of network devices. Transfer the configuration files to the network devices for configuration updates, or download the configuration files from the network devices for backup or analysis.
Firmware upgrade for IoT devices: Due to its simplicity and efficiency, the TFTP protocol has become a commonly used protocol for firmware upgrade of IoT devices.
4 The basic workflow of the TFTP protocol
Request sending: The client sends a read request (RRQ, Read Request) or a write request (WRQ, Write Request) to the server. These requests contain the file name to be read or written and the transmission mode (such as binary or ASCII code).
Establishing connection: After receiving the request from the client, the server, based on the file name and transmission mode in the request, opens the corresponding file (for write requests) or prepares to send the file data (for read requests), and sends a confirmation message to the client, thereby establishing the connection.
Data transmission: In the case of a write request, the client starts sending file data to the server, and the server receives and writes the file. The data is sent in the form of data blocks, with each data block typically being 512 bytes (but can be adjusted according to network conditions).
In the case of a read request, the server starts sending file data to the client, and the client receives and saves the file. Similarly, the data is also sent in the form of data blocks.
Response and confirmation: Whenever the client or server sends a data block, the receiving party sends an acknowledgment packet (ACK, Acknowledgment) to confirm the receipt of that data block. This acknowledgment packet contains the number of the received data block to ensure the order and integrity of the data.
Continuing transmission or ending: Based on the acknowledgment packet, the sender will continue to send the next data block until the entire file is transmitted. If an error occurs during the transmission process, the server will send an error information packet (ERROR) to the client, interrupting the transmission process.
Closing connection: After the file transmission is completed, the client and server will close the connection.
5 TFTP Protocol Message Analysis
Common operation codes:
1: Read Request (RRQ), used to request to read a file from the server.
2: Write Request (WRQ), used to request to write a file to the server.
3: Data (DATA), used to transmit file data.
4: Acknowledgment (ACK), used to confirm the received data blocks.
5: Error Information (ERROR), used to report errors that occur during the transmission process.
The message format of common operation codes is as follows:
Message type | Message format | Operation code | Other key fields and explanations |
Read Request (RRQ) | The total length is variable, consisting of a 2-byte operation code, a variable-length file name (ending with 1 byte 0), and a variable-length transmission mode (ending with 1 byte 0). | 1 | File name: Name of the file to be read Transmission mode: "netascii" indicates ASCII code mode, "octet" indicates binary mode |
Write Request (WRQ) | The total length is variable, consisting of a 2-byte operation code, a variable-length file name (ending with 1 byte 0), and a variable-length transmission mode (ending with 1 byte 0). | 2 | File name: Name of the file to be read Transmission mode: "netascii" indicates ASCII code mode, "octet" indicates binary mode |
(DATA) | Composed of a 2-byte operation code, a 2-byte data block identifier, and up to 512 bytes of data. | 3 | Data block number: Starts from 1 and is used to identify the sequence of data blocks Data: The actual transmitted file content |
Acknowledgment (ACK) | Composed of a 2-byte operation code and a 2-byte data block identification number | 4 | Data block number: Consistent with the received data block number, used for confirming reception |
(ERROR) | Composed of a 2-byte operation code, a 2-byte error code, and a variable-length error message (ending with 1 byte of 0) | 5 | Error code: Clearly identify the error type Error message: Provide a detailed description of the error situation |
Message example:
Client read request message:
|Message parsing||Original message|Server response message:
|Message parsing|
|Original message|Client response message:
|Message parsing|
|Original message|Server response message:
|Message parsing|
|Original message|Client response message:
|Message parsing|
|Original message|6 The implementation process
Next, we implement the TFTP protocol for file reading on the W55MH32. Note: The test instances require that the PC and W55MH32 be on the same network segment.
In the main function, the do_tftp_client() function is called to continuously check and handle the status of the TFTP client, and based on the read result (success or failure), enter the corresponding processing state.
1. do_tftp_client(SOCKET_ID, ethernet_buf);The do_tftp_client() function is as follows:
1. void do_tftp_client(uint8_t sn, uint8_t *buff)After entering the do_tftp_client() function, the TFTP client processing begins. The steps are as follows:
Step 1: TFTP initialization
The TFTP_init() function is called to initialize the TFTP client. The parameters sn and buff represent the socket number and socket buffer, respectively.
1. void TFTP_init(uint8_t socket, uint8_t *buf)
1. static void init_tftp(void)Step 2: Send TFTP Read Request
When tftp_read_flag is 0, it indicates that the read request has not been sent yet. At this point, print the IP address of the TFTP server and the file name to be read, and then call the TFTP_read_request() function to send the read request to the server. After sending the request, set tftp_read_flag to 1, indicating that the request has been sent.
1. void TFTP_read_request(uint32_t server_ip, uint8_t *filename)Step 3: Run the TFTP protocol and handle the results
When tftp_read_flag is 1, call the TFTP_run() function to handle the TFTP protocol operation. Based on the returned tftp_state, determine the result: if it is TFTP_SUCCESS, print the success message and enter an infinite loop; if it is TFTP_FAIL, print the failure message and enter an infinite loop.
The TFTP_run() function is as follows:
int TFTP_run(void)When processing the received TFTP data packets, the recv_tftp_packet() function is called first.
The recv_tftp_packet() function is as follows:
1. static void recv_tftp_packet(uint8_t *packet, uint32_t packet_len, uint32_t from_ip, uint16_t from_port)After entering this function, the first step is to verify the source IP address of the received data packet. Only if it is consistent with the server's IP address will the processing continue; otherwise, it will directly return. Then, the operation code (opcode) is obtained from the data packet. Based on the obtained opcode, the corresponding processing function is called: if it is a TFTP read request (RRQ), the recv_tftp_rrq() function is called; if it is a write request (WRQ), the recv_tftp_wrq() function is called; for the received data packet, the recv_tftp_data() function is called; the confirmation of the data packet is handled by the recv_tftp_ack() function; the OACK packet is handled by the recv_tftp_oack() function; if an error data packet is encountered, the recv_tftp_error() function is called to parse the error code and error information. Finally, the g_progress_state is returned to indicate the current status of the TFTP operation.
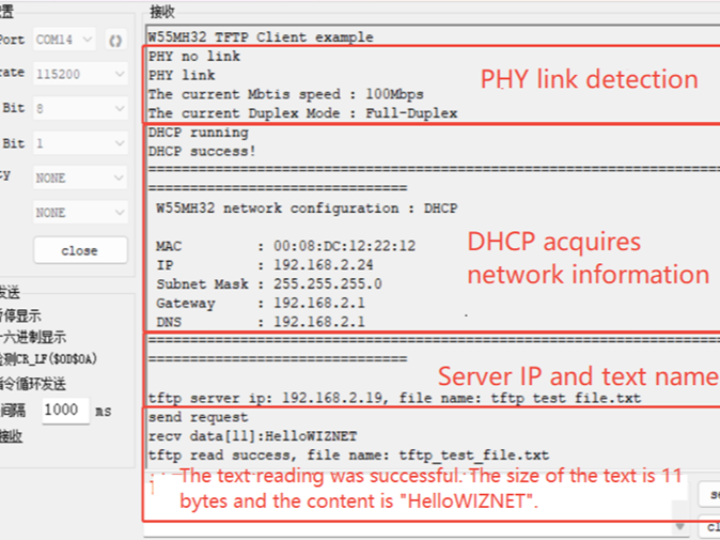
7 Run results
After the burning routine is executed, the PHY link detection is carried out first, followed by the DHCP process for obtaining the network address result. Finally, the server IP and text name are printed, and the text content is read, as shown in the following figure:
8 Summary
This article explains how to implement the TFTP protocol on the W55MH32 chip. Through practical examples, it details the process of obtaining text files from the server using the TFTP client mode, covering the core steps such as TFTP initialization, sending read requests, running the protocol and handling results. The article also analyzes the introduction, features, application scenarios, basic workflow and message parsing of the TFTP protocol, helping readers understand its practical application value in file transfer.
The next article will focus on the SNMP protocol, analyzing its core principles and applications in network management, and explaining how to implement the SNMP function on related devices. Stay tuned!
WIZnet is a non-chipfoundry semiconductor company founded in 1998. Its products include the Internet processor iMCU™, which adopts TOE (TCP/IP Offloading Engine) technology and is based on a unique patented fully hardwired TCP/IP. iMCU™ is designed for embedded Internet devices in various applications.
WIZnet has over 70 distributors worldwide, with offices in Hong Kong, South Korea, and the United States, providing technical support and product marketing.
The region managed by the Hong Kong office includes: Australia, India, Turkey, and Asia (excluding South Korea and Japan).
