Chapter 39: Implementing SHA (SHA-1 / SHA-256) with WIZnet W55MH32 Hardware Encryption
Chapter 39: Implementing SHA (SHA-1 / SHA-256) with WIZnet W55MH32 Hardware Encryption
1. Introduction
The WIZnet W55MH32 is a high-performance microcontroller featuring an ARM Cortex-M3 core operating at up to 216 MHz. It integrates a hardware encryption engine supporting various cryptographic algorithms, including SHA-1 and SHA-256. Leveraging the hardware SHA capabilities of the W55MH32 enhances data integrity and security in embedded applications, especially those involving network communications.
This application note provides an overview of SHA functions, their role in SSL/TLS protocols, and practical applications within the W55MH32 environment.
2. Overview of SHA
Secure Hash Algorithm (SHA) is a cryptographic function that transforms input data of any length into a fixed-length digest (or hash). The WIZnet W55MH32 supports SHA-1 (160-bit digest) and SHA-256 (256-bit digest) through its hardware encryption engine, providing accelerated, low-power hashing operations.
SHA is a one-way function — it is computationally infeasible to recover the original input from its hash or to find two different inputs that produce the same hash (collision resistance).
SHA processing flow in microcontrollers
The SHA hardware engine or driver typically exposes a three-phase function structure:
1. Start
This phase initializes the SHA engine and selects the desired hash algorithm (SHA-1 or SHA-256). It sets up internal state variables, clears any previous data, and prepares the hardware engine to accept new data for processing.
2. Update
This phase feeds the input data to the SHA engine in one or more blocks. The data can be provided in segments, which allows for hashing of large datasets or streaming data without loading the entire dataset into memory. The engine updates its internal state as each block is processed.
3. Finish (or Final)
This phase finalizes the hashing operation. It applies padding if necessary, completes the internal digest calculation, and outputs the final hash value. The digest represents the fingerprint of all the data provided during the update phase.
Benefits of start-update-finish structure
Allows hashing of data in segments, which is especially useful for large files, streamed data, or network packets.
Enables efficient use of hardware accelerators by processing data in manageable blocks.
Reduces memory usage, as there is no need to hold the entire message in memory at once.
Supports real-time and incremental hashing workflows common in secure communications and data verification.
Integration in W55MH32
The SHA hardware engine of the W55MH32 is accessed through dedicated registers or driver APIs.
The engine handles padding and block alignment internally during the finish phase.
Using hardware SHA significantly accelerates hash computations, particularly for applications involving large data volumes or real-time processing.
3. Role of SHA in SSL/TLS Protocols
In SSL/TLS protocols, SHA functions are utilized for:
Message Integrity: Ensuring that messages have not been altered during transmission by generating and verifying message digests.
Certificate Verification: Validating digital certificates through hash functions combined with digital signatures.
Key Derivation: Assisting in the generation of session keys from shared secrets using pseudo-random functions (PRFs).
By offloading these operations to the W55MH32's hardware SHA engine, systems can achieve faster processing and reduced CPU load, leading to improved performance and energy efficiency.
4. Additional Applications of SHA in W55MH32 Systems
Beyond SSL/TLS, SHA functions in the W55MH32 can be employed in various scenarios:
Secure Firmware Updates: Verifying the integrity of firmware images before installation.
Password Storage: Hashing passwords for secure storage and authentication.
Digital Signatures: Creating and verifying digital signatures for secure communications.
Data Integrity Checks: Ensuring the consistency and integrity of data stored or transmitted.
5. Progress
For activating this feature, it is required the following steps to operate.
Step 1: Header files
For using SHA features, it is required to include wiz_sha.h file to operate the SHA function in WIZnet's encryption library.
Step 2: SHA procedures
In SHA function, it includes three main function for hashing the message.
The start function is used to activate SHA function.
// SHA1 start function
WIZSHA1_Starts(&ctx);
// SHA256 start function
WIZSHA256_Starts(&ctx2);For providing a better processing to the MCU, it includes update function to add more data for SHA processing.
// SHA1 Update function and get data from TestSHA with the data size of 100 bytes
WIZSHA1_Update(&ctx, TestSHA, 100);
//SHA256 Update function and get data from buf0 with the data size of 64 bytes
WIZSHA256_Update(&ctx2, buf0, 0x40);Finally, it provides the final processing all the inputted data and get the result.
// SHA1 finish function and save it in digest variable
WIZSHA1_Finish(&ctx, digest);
// SHA256 finish function and save it in digest variable
WIZSHA256_Finish(&ctx2, digest);Step 3: Main Code
In this Main code, it contains the SHA-1 and SHA256 testing method with example.
void SHA_Update_Test()
{
uint32_t i;
WIESHA1_Context ctx;
WIESHA1_Context ctx2;
uint8_t digest[20];
uint8_t buf[64];
unsigned char TestSHA1[100] = "12345678901234567890123456789012345678901234567890123456789012345678901234567890";
printf("Test the sha function...\n");
printf("SHA 160 test data is \n%s\n", TestSHA1);
WIESHA1_Update(&ctx, TestSHA1, 100);
WIESHA1_Finish(&ctx, digest);
printf("SHA 160 result is \n");
for (i = 0; i < 20; i++)
{
printf("%02x", digest[i]);
}
printf("\n\n");
memset(digest, 0, 20);
memset(buf, 'a', 64);
memset(buf, 'b', 0x30);
printf("SHA 256 first set of test data is \n");
for (i = 0; i < 64; i++)
{
printf("%02x", buf[i]);
}
WIESHA256_Update(&ctx2, buf, 0x30);
printf("\nSHA 256 second set of test data is \n");
for (i = 0; i < 64; i++)
{
printf("%02x", buf[i]);
}
printf("\n\n");
WIESHA256_Update(&ctx2, buf, 0x30);
WIESHA256_Finish(&ctx2, digest);
printf("The sha_256 result is \n");
for (i = 0; i < 32; i++)
{
printf("%02x", digest[i]);
}
printf("\n\n");
}Step 4: Testing Result
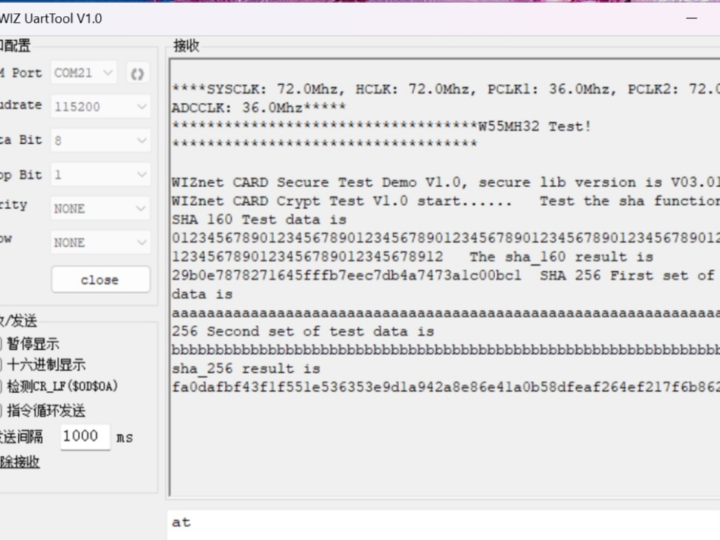
After the program has been downloaded to the W55MH32's EVB, it shows the following results. Result from Serial terminal:
Result from Serial terminal:
It shows the result as follow.
Reference code
Copy
SHA-1 : 29b0e7878271645fffb7eec7db4a7473a1c00bc1
SHA256: fa0dafbf43f1f551e536353e9d1a942a8e86e41a0b58dfeaf264ef217f6b862aPython Result for SHA1 and SHA256
By comparing from the python codes, it shows the hardware function for SHA is working without any problem.
The comparison result is consistent with that of the python result, indicating that the hardware SHA function is normal.
Conclusion
The WIZnet W55MH32 microcontroller's hardware support for SHA-1 and SHA-256 provides robust tools for enhancing security in embedded systems. By integrating SHA functions into applications, developers can ensure data integrity, authenticate communications, and protect against unauthorized modifications, all while benefiting from the performance advantages of hardware acceleration. For detailed implementation examples and further information, refer to WIZnet's official documentation and example projects.
