ARPoLAN: Network Monitoring And Security Tool
ARPoLAN is a tool for network scanning and ARP spoofing using the Atmega32u4 and W5500
- Network Scanning
- ARP Spoofing
- HID Functionality
- Real-tim
Software Apps and online services
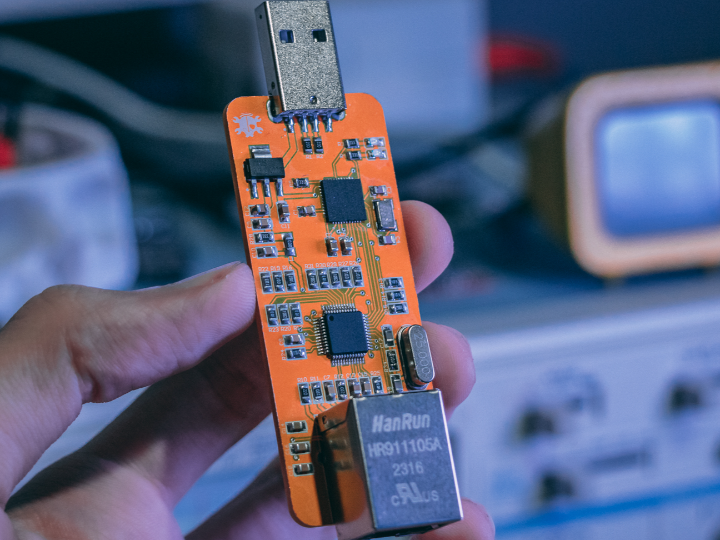
Today, we're excited to introduce ARPoLan, a project that leverages the power of the Arduino Pro Micro and the W5500 Ethernet module. This versatile device can perform network scanning, ARP spoofing, and even act as a local Rubber Ducky. Let's dive into how this network security tool was built and tested.
Features & Components
ARPoLan combines several powerful components to deliver impressive capabilities:
- Network Scanning: Discover devices on the local network by sending ARP requests and collecting responses.
- ARP Spoofing: Perform ARP spoofing attacks to intercept and manipulate network traffic.
- HID Functionality: Utilize the Atmega32u4's USB HID capabilities for additional attack vectors.
- Real-time Monitoring: Visual and serial indicators for attack detection and network activity.
Getting Started
The PCB for ARPoLan was designed using Altium Designer, featuring a simple yet efficient two-layer layout. Here’s a breakdown of the components used:
- Atmega32u4 Microcontroller: Handles USB communication and processing tasks.
- W5500 Ethernet Module: Provides reliable network connectivity with an integrated hardware TCP/IP stack.
- 25 MHz Crystal Oscillator: Ensures precise timing for network operations.
- RJ45 Ethernet Socket: Facilitates network connections with integrated status LEDs.
- LM1117 Voltage Regulator: Supplies a stable 3.3V power to the W5500.
- USB A Port: Allows for easy programming and data transfer.
- Passive Components: Capacitors and resistors for power stabilization and signal integrity.
Communication between the W5500 and the Atmega32u4 is handled via the SPI protocol, ensuring quick and reliable data transfer.
Schematic
The PCB for ARPoLan was designed using Altium Designer, featuring a two-layer layout optimized for compactness and efficiency. The board integrates all necessary components, ensuring reliable connections between the Atmega32u4 and the W5500.
Connection Table
- Ensure the VCC pin of the W5500 is connected to a 3.3V power supply, as the module operates at 3.3V logic levels.
- The SS (Slave Select) pin can be connected to any digital pin on the Arduino Pro Micro, but it must be defined correctly in the code.
- Make sure the GND of the Arduino Pro Micro is connected to the GND of the W5500 module to ensure a common ground.
This setup will enable SPI communication between the Arduino Pro Micro and the W5500 Ethernet module.
Usage
- First Code: Local Rubber Ducky: The first piece of code transforms ARPoLan into a local Rubber Ducky. The Atmega32u4's USB HID capabilities allow it to act like a keyboard or mouse, injecting pre-programmed keystrokes into a connected computer. This was a fun experiment, though it carries potential risks.
- Second Code: ARP Spoofing: Next, the ARP spoofing code was tested. This script injects malicious ARP packets into the network, leveraging the processing power of the Atmega32u4 and the network capabilities of the W5500. While not overly powerful, it demonstrated the device's potential for network security tasks.
- Third Code: Network Scanning: The final code was for network scanning. By sending ARP requests to all IP addresses within a specified range, ARPoLan could identify active devices on the network. This functionality is crucial for network monitoring and penetration testing.
Code & PCB
If you're interested in building this project, the code and schematic are available on GitHub. Simply visit the GitHub repository to download the necessary files. If the project gains attention, the PCB files will also be open-sourced. Feel free to test the code and share your feedback or improvements.
GitHub repository: github.com/cifertech/arpolan
Special Thanks to Our Sponsor: JLCPCB
No project is complete without the right tools and materials. That’s where our sponsor, JLCPCB, stepped in to provide essential support for this project. JLCPCB is a leading provider of high-quality printed circuit boards (PCBs) and PCB assembly services. Simply head over to JLCPCB, upload your PCB design files, select your preferences, and your custom PCBs will be on their way to you in no time. If you sign up using the link in the description below, you’ll receive a $60 new user coupon.
Conclusion
Creating ARPoLan was a fascinating journey into network security and hardware integration. From designing the PCB to writing and testing the code, this project showcased the potential of combining simple yet powerful components to achieve sophisticated functionalities. Stay tuned for future updates and enhancements, and don’t forget to check out the project details on GitHub. If you have any ideas or suggestions, we would love to hear them!
For more information and a detailed project overview, visit the project on Hackster.io and watch the YouTube video.


