W55RP20 TOE vs. LWIP: Network Performance Test with iPerf3
W55RP20 TOE vs. LWIP: Network Performance Test with iPerf3
iPerf3 LwIP code : https://github.com/WIZnet-ioNIC/WIZnet-PICO-IPERF-C/tree/main/examples/iperf3/lwip
iPerf3 TOE code : https://github.com/WIZnet-ioNIC/WIZnet-PICO-IPERF-C/tree/main/examples/iperf3/toe
Network Stability Testing with NPING: SYN Flood Attack Simulation
Introduction
Network security and stability are critical for any system handling data transmission. One way to assess network robustness is by simulating real-world attack scenarios. This post explores how to use NPING to conduct a SYN Flood Attack simulation and analyze network stability under stress.
NPING Download and Installation
You can download NPING as part of the Nmap suite:
Official website: https://nmap.org/nping/
To install on different platforms:
Linux (Debian-based)
sudo apt update && sudo apt install nmapMacOS (via Homebrew)
brew install nmapWindows
Download and install the Nmap package from the official website.
SYN Flood Attack Simulation using NPING
A SYN Flood Attack is a Denial of Service (DoS) attack where an attacker sends multiple TCP SYN packets to a target, exhausting its resources.
Command to Perform SYN Flood Attack
sudo nping --tcp -p 80 --flags SYN --rate 1000 -c 10000 <TARGET-IP>Explanation:
--tcp → Use TCP protocol
-p 80 → Target port 80 (HTTP)
--flags SYN → Set SYN flag to simulate a connection request
--rate 1000 → Send 1000 packets per second
-c 10000 → Send a total of 10,000 packets
<TARGET-IP> → Replace with the actual target IP
Observing Network Stability
While running the SYN flood, monitor the network behavior using:
On the Target System:
netstat -an | grep :80This will show the number of half-open connections.
Using Wireshark/Tcpdump:
Capture packets to analyze the impact:
sudo tcpdump -i eth0 port 80
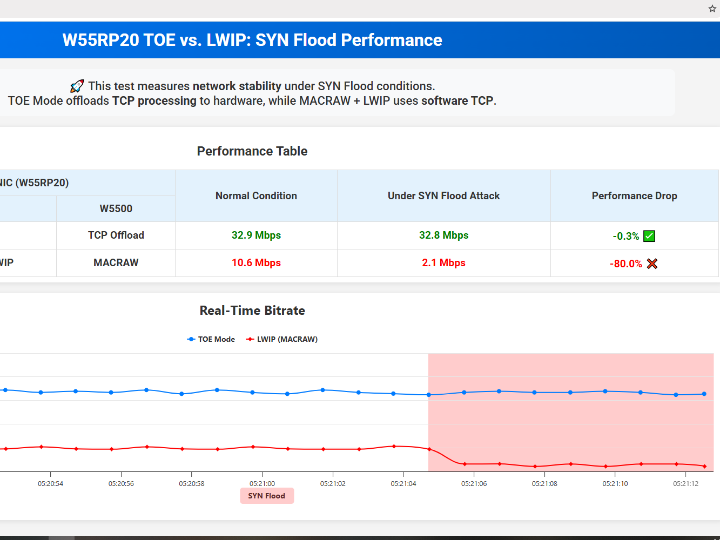
TOE vs. LWIP Performance under SYN Flood Attack
When conducting a SYN flood attack on systems using TOE (TCP Offload Engine) and LWIP (Lightweight IP), significant performance differences were observed:
TOE Performance Drop: Only 0.3%
LWIP Performance Drop: Around 80%
Why is TOE More Resilient?
Hardware Acceleration: TOE handles TCP processing at the NIC level, reducing CPU workload.
Efficient Connection Handling: Unlike LWIP, which relies on software processing, TOE manages large numbers of connections without excessive resource consumption.
Offloaded Packet Processing: SYN flood attacks mainly target the CPU with excessive connection requests. TOE mitigates this by offloading processing tasks to dedicated hardware.
Reduced Interrupt Overhead: LWIP needs frequent CPU interrupts to process packets, whereas TOE processes them with minimal CPU intervention.
TOE Advantages in Network Security
Higher Throughput: Even under attack conditions, TOE maintains stable performance.
Lower Latency: Network applications experience minimal delays.
Better Resource Utilization: Frees up CPU cycles for other critical tasks.
Enhanced DDoS Resistance: TOE handles malicious traffic more efficiently than software-based stacks like LWIP.